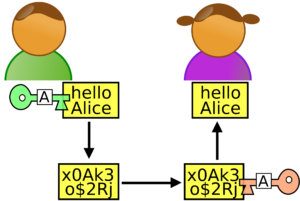
This workshop shows the mathematic foundation of the asymmetric cyphering systems used in nowadays computers. Through some practical activities we will explain differences between public and private key, Kerckhoffs’ principle, Diffie-Hellman algorithm and we will try to break them. This workshop requires the visitors to have some mathematical concepts clear (factorisation, prime numbers), so it is recommended for undergraduate students.